Introduction to Distributed Denial of Service Attacks
Maintaining an uninterrupted online presence is crucial for businesses and individuals in today’s digital landscape. Of all the cyber threats out there, DDoS attacks are hazardous. These are primarily cyber-attacks that flood a network, service, or website beyond what is acceptable and tolerable, quickly making the network, service, or website difficult, if not impossible, for users to access. This cyber-attack can bring enormous productive losses, financial losses, and dents in an organization’s reputation.
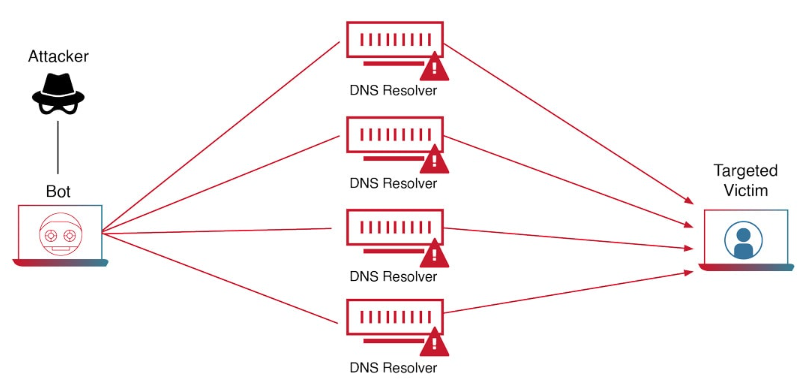
A DDoS attack typically involves a coordinated effort where multiple systems flood the target with traffic. In most cases, this is accomplished with the assistance of a network of hijacked computers—or a botnet. The level of traffic involved in these botnets can be astronomical, and very soon, the target is overwhelmed and cannot process any other traffic.
DDoS attacks are not just about quantity; they can exploit specific weaknesses within the target’s network protocols or applications. This makes them not only disruptive but also challenging to defend against.
These attacks can be categorized into three main types: volumetric assaults, protocol assaults, and application layer assaults. Both types utilize different facets of a network’s infrastructure: Coordinated attempts to inflict maximum damage in any form with various techniques and tools.
Anyone managing online services must grasp how DDoS attacks work. The outcome of such an attack is severe, resulting in losses of customers’ trust and losses incurred by the business.
As these attacks become more elaborate and large-scale, so must the solutions that protect one’s network and data. Creative and proper approaches are initial steps; a well-balanced network architecture and adequate monitoring tools are ways to avoid losses during DDoS attacks.
The Mechanics of DDoS Attacks
DDoS attacks rely on exploiting the limited resources of a network or server, making it difficult for legitimate users to access services. These attacks generally fall into three categories:
- Volumetric Attacks: These attacks focus on overwhelming the target’s bandwidth with enormous data. Excessive traffic quickly depletes available resources, leading to service outages. Methods such as DNS amplification or UDP floods are commonly used to achieve this.
- Protocol Attacks: Also known as state-exhaustion attacks, these target specific weaknesses in network protocols like TCP/IP. By exploiting these vulnerabilities, they consume server resources and intermediate communication devices, effectively crippling the target. Examples include SYN floods and Ping of Death attacks.
- Application Layer Attacks: These attacks target the top layer of the OSI model, focusing on specific applications rather than the entire network. They resemble real ordinary users’ behavior; as such, they are not easy to identify. This attack is most familiar with web servers, which focus on functions such as login pages or search fields to deny service. Some of them are HTTP floods and Slowloris attacks.
All respective categories operate using different techniques and resources, adding up to the optimal level of disruption. While volumetric attacks aim to exhaust bandwidth, protocol attacks drain server resources, and application layer attacks disrupt specific functionalities.
The nature of these mechanisms must be considered to create efficient defense strategies. Platforms like firewalls, rate limiting, and other high-end enabling monitoring tools help detect these evils. To constantly evolve, a completely new area of attack vectors and defense techniques are developed slowly and consistently to adapt to this constant technological change.
Typical Targets and Consequences
Certain online services are desirable targets for DDoS attacks due to their high visibility and dependency on continuous availability. Websites that experience high traffic, such as those belonging to media outlets or streaming services, are prime targets.
Gaming services, where uninterrupted access is critical for user experience, also fall victim. Financial institutions, with their extensive online transactions and e-commerce platforms, which rely on constant uptime for sales, are also frequently targeted.
The repercussions of a successful DDoS attack are severe. For businesses, the immediate consequence is often significant revenue loss due to the unavailability of services. Long-term effects tend to be more catastrophic than short-term ones because clients stop patronizing a firm they no longer trust. Also, interruption of services will cause customers to develop a negative attitude towards the company, culminating in complaints.
From a technical standpoint, the attacked service might experience data breaches if the attackers exploit vulnerabilities during the downtime. Recovering from a DDoS attack often involves substantial financial and resource investment, from restoring services to implementing improved security measures to prevent future incidents.
This includes the direct costs of mitigating the attack and repairing the damage and the indirect costs related to business interruptions and lost opportunities.
Organizations that heavily depend on their internet presence should be cautious when implementing advanced security and preparing for DDoS attacks. Because of these attacks’ ever-growing sophistication and expansion, any defense measures instituted today require constant change and update.
Recognizing a DDoS Attack
Detecting a DDoS attack early can significantly reduce its impact. Common indicators include unexpectedly slow network speeds and intermittent website availability. If an ordinarily responsive website starts to lag or becomes inaccessible, it could signal an ongoing DDoS attack.
Additionally, an abrupt spike in traffic from various IP addresses may indicate that a botnet is at play. Other indicators include One-rapid calls to a specific endpoint, service, or API or too many error calls indicating service saturation.
These symptoms are usually more manageable for network administrators to detect, and they use various tailored devices. Traffic monitoring solutions can be crucial as they deliver real-time traffic flow and traffic type data.
Some particular patterns, for instance, increased request frequency or excessive requests originating from specific sources, can generate alerts. Some highly developed monitoring systems are integrated with machine learning algorithms to recognize exceptional patterns different from regular traffic.
Other than traffic research, logging instruments can provide additional information by assessing the requests’ frequencies and error percentages. These logs are handy for identifying when an attack started and how far it spread.
It is also important to note that intrusion detection systems may help identify other potentially illicit activities that, while not constituting a DDoS attack per se, may lead up to one.
The identification phase needs to be swift so that countermeasures can be effectively implemented. One of the simplest methods is to use rate limiting to limit traffic, and firewalls and other security gadgets should permanently be configured to block nasty IP addresses in the network.
Thus, when organizations familiarize themselves with the features of a DDoS attack, they can contain it before the effects are compounded.
Strategies for Prevention and Mitigation
Implementing a multi-layered defense approach is an effective strategy for preventing and mitigating DDoS attacks. The key idea is to ensure high network performance and fault tolerance by designing the network with multiple layers and equipment to achieve load balancing. The traffic tendencies are also monitored so that necessary action is taken if there is anything suspicious.
One is regulating the traffic rate, where the attackers reduce the traffic speed. Positive inspection is, therefore, vital, as is the use of firewalls and intrusion detection systems to deter invaders. Internet protocol addresses and acknowledges particular rigorous undertakings. They can detect specific threats that may be used by an attacker or used for defense in depth.
Anti-DoS can filter and block potentially negative connections before they impact the target systems. Some organizations also subscribe to cloud-based DDoS protection services that afford the required level of protection for a growing number of clients. Such services can observe more traffic and respond to threats immediately; thus, they are effective for large enterprises.
Another vital prevention is a security audit and vulnerability assessment. These evaluations help define probable areas of vulnerability in the network that intruders may exploit. Basic steps like patching and updating software Counterparts uses to eliminate recognized risks are also important factors.
Training staff to recognize the signs of a DDoS attack and respond appropriately is equally essential. An informed team can activate response protocols quickly, reducing the potential damage.
Lastly, developing an incident response plan that outlines specific steps to take during an attack ensures that everyone knows their role and responsibilities, facilitating a coordinated and effective response.
Emerging Trends in DDoS Attacks
As technology becomes even more sophisticated, new approaches and instruments for DDoS attacks are expected to appear. The major uses the Internet of Things (IoT) devices’ resources. These devices are usually not very secure and are easy to hijack and use to create enormous botnets. These botnets can then be used to launch large-scale synchronized attacks and, therefore, become hard to stop.
Lastly, artificial intelligence is being used in DDoS attack frameworks. Criminals are now using AI to devise better attack plans. As AI can power these, analyzing and tweaking execution methods in real time will make them more challenging to counter.
Furthermore, a vigorous trend shows that attackers choose specific industries and services using particular approaches. For example, widespread work from home increases cyber attackers’ interest in products such as collaboration software and VPNs. Breaking these critical services can cause significant operational disruption in an organization.
Presumably, new issues will also surge with the emergence of 5G technology. Notably, the following challenges have been identified as likely to occur due to technological advancement. While 5G networks will deliver faster and more secure connections, the assailants might take less time to exploit loopholes in this type of network.
These emerging trends indicate that organizations must be more alert and adapt new methods of defending against the complex DDoS attacks that are gradually presented.