Introduction to IP Addresses
Every device that connects to the Internet requires basic knowledge about IP addresses in the present technological era. A network device stands unique with an IP address that lets it speak with other devices. The Internet Protocol (IP) addresses exist in two fundamental versions, including public and private addresses.
The purpose of each IP address type differs from others, and each IP address has its own specific characteristic set. Every device interacting with external networks through the Internet requires a public IP address as its identification certificate. The Internet Service Providers (ISPs) give out these addresses so that visitors to your network can see them.
In contrast, private IP addresses are utilized within local networks, such as those in homes or businesses, to manage and identify devices internally without being exposed to the broader Internet.
The difference between IANA and Regional and Local authorities determines network design principles and security standards. Proficiency in different IP address types is essential for network administrators because it leads to more effective management regardless of individual or corporate requirements. Understanding essential IP addressing principles increases because digital communication keeps expanding.
Characteristics of Public IP Addresses
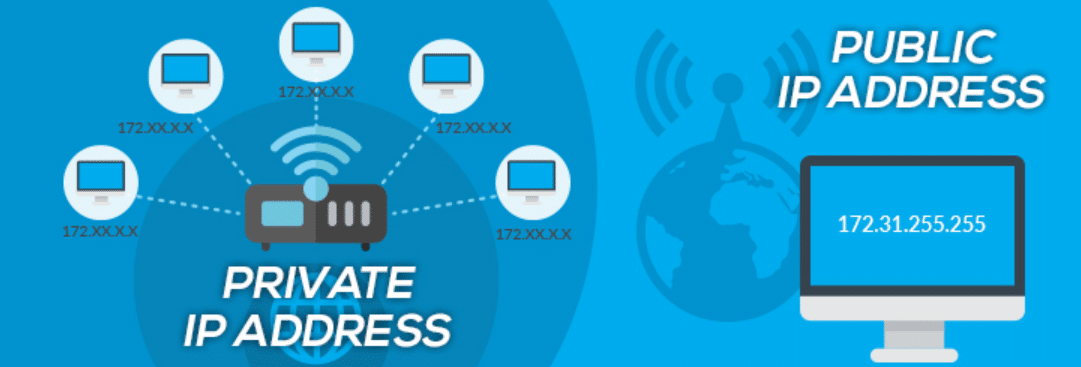
Devices that connect to the Internet need public IP addresses to function as their unique addressable labels for all devices worldwide. Public IP addresses receive their distribution from Internet Service Providers before they enable networking communication between devices accessing different networks.
Internet infrastructure relies on devices that use public IP addresses as they enable hosting websites, sending emails, and accessing remote services.
The outstanding characteristic of public IP addresses stems from their unique identification across all global networks. Each public IP address is distinct and cannot be duplicated, ensuring that data is correctly routed to its intended destination.
This uniqueness is managed through a hierarchical allocation system involving regional internet registries that oversee address distribution in specific geographic areas.
Public IP addresses can be either static or dynamic. Static addresses remain constant over time and are often used for servers or other resources that require a consistent address.
On the other hand, dynamic addresses can change periodically and are typically assigned to consumer devices by ISPs using Dynamic Host Configuration Protocol (DHCP). This flexibility helps optimize the use of available address space.
While public IP addresses enable extensive connectivity, they also have certain risks. Because these addresses are visible to the entire Internet, devices using them can be targeted for attacks. Defensive systems such as firewalls and intrusion detection systems provide the network security needed to block possible security threats.
Public IP addresses combine for applications to determine geographical locations. Computing the geographic location of devices becomes possible by analyzing assigned addresses for purposes ranging from advertising to content delivery systems.
Public IP addresses are essential building blocks for internet functionality. They make effortless communications between numerous worldwide devices and services possible.
Features of Private IP Addresses
Private IP addresses are designated for use within local networks, such as those found in homes, offices, and other private environments. Private IP addresses serve two essential network functions which identify devices inside locked networks and also aid network management while preventing outside internet access.
The Internet Assigned Numbers Authority (IANA) established three standard private IP address blocks, which cover 192.168.0.0 to 192.168.255.255, 10.0.0.0 to 10.255.255.255 and 172.16.0.0 to 172.31.255.255.
The central benefit of private IP addresses is that they allow organizations to recycle the same numbers among various internal local networks. This reuse is possible because private IPs are not routable on the public Internet, meaning they remain isolated within their respective networks.
As a result, there is no risk of IP address conflicts or shortages within the global address pool. Private IPs serve network administrators well because they efficiently manage numerous devices in localized environments.
The internal network communication of computers, printers, smartphones, and smart home devices depends upon private IP addresses. This internal communication is often managed through a router, which assigns private IP addresses to each connected device via the Dynamic Host Configuration Protocol (DHCP).
In addition to promoting efficient network management, private IP addresses enhance security by keeping internal devices hidden from external threats. Devices with private IPs cannot be accessed directly from the Internet, reducing the likelihood of unauthorized access or cyberattacks.
This isolation allows network administrators to implement additional security measures, such as firewalls and access controls, to protect sensitive information and maintain a secure network environment.

Security Considerations
Devices with public IP addresses are more exposed to potential threats from external sources, as these addresses are visible on the Internet. Protection against these security threats demands the establishment of strong security measures.
Internetworks become protected from external threats through firewalls because these systems filter traffic to prevent unauthorized access. The combination of IDS and IPS systems is a protective tool that tracks abnormal network traffic and activates appropriate responses.
For devices using private IP addresses, the isolation from the public Internet provides an inherent layer of security. Since these addresses are not accessible from outside the local network, it reduces the risk of cyberattacks.
However, internal security should not be overlooked. Network administrators must activate robust security protocols that combine powerful passwords with encryption and system update procedures to defend against vulnerabilities within their network.
Protecting IP addresses requires network segmentation, which is an essential practice. When networks are broken into separate segments using security level differences, controlling malware propagation and blocking access to critical areas becomes possible. VPNs function as secure network solutions, establishing protected pathways across the Internet to ensure data privacy and confidentiality.
Every user should learn to follow best practices which protect network security. Organizational training about security threats and appropriate internet behaviours combined with proper device procedures reduce the frequency of personnel mistakes which trigger security incidents.
Activities that monitor and log network functions to detect security threats by collecting valuable information. Administrative personnel solve issues by keeping detailed records and frequent log examinations.
Each public and private IP address needs customized security preparations that understand its vulnerability risks and role inside network systems. Any digital communication network depends on secure IP addresses to ensure safety and integrity.
Practical Applications
Public IP addresses are critical in enabling devices to communicate with external networks. Online platforms find crucial support through these addresses when they host websites and operate email servers with gaming platforms.
Company services depend on these addresses to enable users worldwide to interact with their products, which becomes crucial for companies with global market ambitions. For example, an e-commerce website must have a public IP address to facilitate transactions and customer interactions from various locations.
On the other hand, private IP addresses are tailored for use within local networks, offering a practical solution for internal communication and resource sharing. In a household, private IP addresses enable devices such as computers, printers, and smart home devices to connect seamlessly.
For instance, multiple computers within the same network can access a printer with a private IP address without needing a public connection.
In a corporate setting, private IP addresses help manage large numbers of devices efficiently. Employees can share files, access intranet services, and use networked peripherals like printers and scanners without exposing these resources to the Internet. Private IP addresses help network administrators handle their systems through simple identification and troubleshooting of devices found in local networks.
Virtual Private Networks (VPNs) enable secure remote connections between private network domains and public locations worldwide through their capability to connect private and public IP addresses. Private workers benefit substantially from safe access to company resources through VPNs.
Learning about public and private IP addresses enables the creation of more secure and functional network systems for residential and corporate networks.
Conclusion
Deciding between public and private IP addresses hinges on the specific needs of your network. Global Internet operations need public IP addresses which serve as essential network connection components for all external-facing devices and services thus supporting organizations that target worldwide customers.
Private IP addresses deliver peak network management and security features for internal communication; thus, they work best in homes and organizations wishing to protect internal data from outside threats.
Planned usage of both IP address types enables optimal network performance levels and security benefits, leading to secure digital communications and managed resources. Your ability to make network decisions becomes sharper through comprehending how public and private IP addresses operate and function in different scenarios.